IN THIS ARTICLE
What is Cryptojacking?
 Cybercriminals have begun to seize the opportunity, secretly mining cryptocurrency on other people’s computers without their permission. The process is known as “cryptojacking,” and it occurs when hackers install malicious software on a device, typically via infected websites, email attachments, or apps. The software operates in the background, utilizing the device’s power and resources to generate digital currency for the hacker. This can significantly slow down the device, increase the electricity bill, and even cause irreversible damage.
Cybercriminals have begun to seize the opportunity, secretly mining cryptocurrency on other people’s computers without their permission. The process is known as “cryptojacking,” and it occurs when hackers install malicious software on a device, typically via infected websites, email attachments, or apps. The software operates in the background, utilizing the device’s power and resources to generate digital currency for the hacker. This can significantly slow down the device, increase the electricity bill, and even cause irreversible damage.
Armor Cryptomining Protection Feature
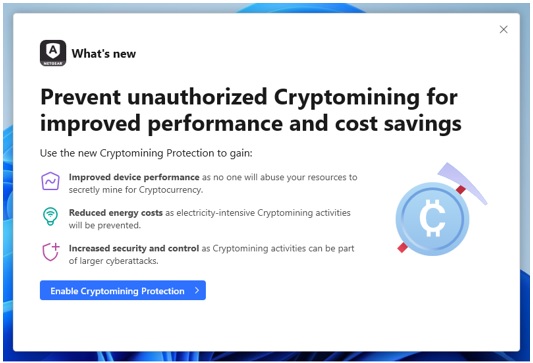
Introducing Cryptomining Protection, NETGEAR Armor’s new cryptomining management feature, which allows users to protect against malicious cryptojacking while also managing their own legitimate cryptomining initiatives on their Windows PCs.
Cryptomining Protection ensures Armor users are aware of and protected from unauthorized system breaches by blocking cryptojacking malware that attempts to exploit system resources. At the same time, because some users want to engage in legitimate cryptomining activities, Cryptomining Protection serves as a unique management tool, allowing them to monitor and decide what should be kept running and what should be stopped.
Get Armor for Cryptomining Protection & Management
To get Cryptomining Protection, download NETGEAR Armor for your Windows device click below:
Learn more about NETGEAR Armor
In our digital age, safeguarding our online identity is of the utmost importance. The ever-expanding digital domain has come to include our private data, sensitive documents, online behavior and, more recently, digital assets in the form of cryptocurrency.
With the advent of cryptomoney, a relatively new cyber threat has emerged – cryptojacking, in the form of cryptomining malware. This malware strain piggybacks on your device’s processing power to mine cryptocurrency without your knowledge, taking a significant toll on your device’s performance and potentially paving the way for other, more severe security risks.
Recognizing this threat, Bitdefender Total Security now encompasses a cutting-edge cryptomining protection feature. Designed with the everyday user in mind, this feature protects your device from cryptomining malware, ensuring an unfettered online experience.
Enabling Cryptomining Protection on Your Device:
As mentioned, Bitdefender Total Security will notify you of the feature’s availability, allowing you to activate it on the spot, and give you a brief presentation of its capabilities and benefits. This is the easiest way to turn on cryptomining protection for your device.
However, if you missed the notification, you can find it under the “Protection” category in the main window. You can easily enable Cryptomining Protection by flipping the corresponding switch and configure it by clicking the “Settings” button.
Setup: Block All Detected Cryptomining Activity
The first Cryptomining Protection setting in the menu, called “Block all Cryptomining activities,” as its name suggests, blocks all detected cryptomining activities automatically and acts accordingly to prevent further attempts or propagation. Unless specified, this setting will be chosen by default upon activating the feature.
The setting also lets you receive notifications each time an activity is blocked on the device; or you could opt for a quieter approach that tells the feature to operate stealthily, notifying you every 24 hours via a pop-up summary.
It’s worth mentioning that the first setting is recommended for users who don’t plan to run cryptomining activities on their devices.
Setup: Manage Cryptomining Activities Manually
The second setting, “Detect Cryptomining activities,” provides a more hands-on approach. Upon choosing this setting, the feature detects matching activities on the system and informs you about them, but without taking further action automatically.
You can then review the event and decide how to proceed, whether by allowing the activity to unfold on your system or blocking it. Choosing the latter will kill the unwanted process and disinfect your machine to prevent it from restarting.
Advanced users can benefit from a third option, allowing them to configure exceptions to exclude from the scan. This could be useful if you want to mine cryptocurrency on your device and block all other detected activities automatically.



